Discounted Certified Ethical Hacker | CEH v10 Course
Certified Ethical Hacker v10 (CEH) – 10% OFF
The worlds most advanced ethical hacking course with 20 of the most current security domains an ethical hacker will want to know when planning to beef up the information security posture of their organization. In 20 comprehensive modules, the course covers over 270 attack technologies, commonly used by hackers.
Our security experts have designed over 140 labs which mimic real time scenarios in the course to help you “live” through an attack as if it were real and provide you with access to over 2200 commonly used hacking tools to immerse you into the hacker world.
The goal of this course is to help you master an ethical hacking methodology that can be used in a penetration testing or ethical hacking situation. You walk out the door with ethical hacking skills that are highly in demand, as well as the globally recognized Certified Ethical Hacker certification!
What Our Students Say
Can You Spot the Hacker?
iLabs Demo:
Meet Your Instructor
- 100% Compliance to NICE 2.0 Framework
- Coverage of latest Malware
- Lab environment simulates a real-time environment
- New Modules: Vulnerability Analysis & IoT Hacking
- Covers latest hacking tools (Based on Windows, MAC, Linux, and Mobile)
- ANSI Accreditation
- Focus on Emerging Attack Vectors (e.g., Cloud, AI, ML, etc.)
- Hands-on Program
- Hacking Challenges at the End of Each Module
- Inclusion of complete Malware Analysis Process
Course Description
The Certified Ethical Hacker (CEH v10) program is a trusted and respected ethical hacking training Program that any information security professional will need. Since its inception in 2003, the Certified Ethical Hacker has been the absolute choice of the industry globally. It is a respected certification in the industry and is listed as a baseline certification on the United States Department of Defense Directive 8570. The CEH exam is ANSI 17024 compliant adding credibility and value to credential members.
CEH is used as a hiring standard and is a core sought-after certification by many of the Fortune 500 organizations, governments, cybersecurity practices, and a cyber staple in education across many of the most prominent degree programs in top Universities around the globe.
Hundreds of Thousands of InfoSec Professionals as well as Career Starters have challenged the exam and for those who passed, nearly all are gainfully employed with successful careers, but the landscape is changing. Cyber Security as a profession is evolving, the barrier to entry is rising, the demand for Skilled Cyber professionals continues to grow, but it is being refined, demanding a higher level of skill and ability.
EC-Council raises the bar again for ethical hacking training and certification programs with the all-new CEH v10!
This course in its 10th iteration, is updated to provide you with the tools and techniques used by hackers and information security professionals alike to break into any computer system. This course will immerse you in a “Hacker Mindset” in order to teach you how to think like a hacker and better defend against future attacks.
It puts you in the driver’s seat with a hands-on training environment employing a systematic ethical hacking process.
You are constantly exposed to creative techniques of achieving optimal information security posture in the target organization; by hacking it! You will learn how to scan, test, hack and secure target systems. The course covers the Five Phases of Ethical Hacking, diving into Reconnaissance, Gaining Access, Enumeration, Maintaining Access, and covering your tracks.
The tools and techniques in each of these five phases are provided in detail in an encyclopedic approach and absolutely no other program offers you the breadth of learning resources, labs, tools and techniques than the CEH v10 program.
Students going through CEH training will learn:
- Key issues plaguing the information security world, incident management process, and penetration testing
- Various types of footprinting, footprinting tools, and countermeasures
- Network scanning techniques and scanning countermeasures
- Enumeration techniques and enumeration countermeasures
- System hacking methodology, steganography, steganalysis attacks, and covering tracks
- Different types of Trojans, Trojan analysis, and Trojan countermeasures
- Working of viruses, virus analysis, computer worms, malware analysis procedure, and countermeasures
- Packet sniffing techniques and how to defend against sniffing
- Social Engineering techniques, identify theft, and social engineering countermeasures
- DoS/DDoS attack techniques, botnets, DDoS attack tools, and DoS/DDoS countermeasures
- Session hijacking techniques and countermeasures
- Different types of webserver attacks, attack methodology, and countermeasures
- Different types of web application attacks, web application hacking methodology, and countermeasures
- SQL injection attacks and injection detection tools
- Wireless Encryption, wireless hacking methodology, wireless hacking tools, and wi- security tools
- Mobile platform attack vector, android vulnerabilities, jailbreaking iOS, windows phone 8 vulnerabilities, mobile security guidelines, and tools
- Firewall, IDS and honeypot evasion techniques, evasion tools, and countermeasures
- Various cloud computing concepts, threats, attacks, and security techniques and tools
- Different types of cryptography ciphers, Public Key Infrastructure (PKI), cryptography attacks, and cryptanalysis tools
- Various types of penetration testing, security audit, vulnerability assessment, and penetration testing roadmap
- Perform vulnerability analysis to identify security loopholes in the target organization’s
network, communication infrastructure, and end systems. - Different threats to IoT platforms and learn how to defend IoT devices securely
Course Outline
- Introduction to Ethical Hacking
- Footprinting and Reconnaissance
- Scanning Networks
- Enumeration
- Vulnerability Analysis
- System Hacking
- Malware Threats
- Sniffing
- Social Engineering
- Denial-of-Service
- Session Hijacking
- Evading IDS, Firewalls, and Honeypots
- Hacking Web Servers
- Hacking Web Applications
- SQL Injection
- Hacking Wireless Networks
- Hacking Mobile Platforms
- IoT Hacking
- Cloud Computing
- Cryptography
EC-Council is dedicated to working with the US Department of Defense to bring the highest standards of Training, Education and Certification to our military.
Independent Accreditation ensures Quality of Certification
EC-Council Certifications are developed to the highest standards and have achieved numerous accreditations including ANSI 17024 for:


To get more information or still have questions:
DoD Directive 8570/ 8140
EC-Council’s Certified Ethical Hacker is an approved baseline certification for the following Cyber Security Service Provider sections:

CSSP Analyst • CSSP Auditor • CSSP Infrastructure Support • CSSP Incident Responder
Information on DoD 8570 can be found at the following DISA website: https://public.cyber.mil/cwmp/dod-approved-8570-baseline-certifications/
Certification to Framework Mappings
A core component of EC-Council Certification development is the Job Task Analysis (JTA) Process we undertake before any certification is built. Major frameworks like the NICE/NIST Framework, NIST 800-171, GCHQ, and others contribute to content areas of each of our programs. As a result, EC-Council Certifications and Training programs are mapped to most major published Frameworks.
EC-Council Maps to the National Initiative for Cybersecurity Education Framework
Download the comprehensive mapping of EC-Council program sections to The Roles and their associated Knowledge, Skills and abilities.
To get more information or still have questions:

EC-Council Cyber Security Certifications and the US NAVY
Six EC-Council Certifications are recognized by the United States Navy in over 100 Cyber Security Job roles, across 18 occupations. Ranging from Commander in Executive Cyberspace Leadership to Cyber Warfare Engineer, Special Agents, Incident Handlers, to Cryptologic Warfare Engineers, Cybersecurity careers with the US NAVY are exciting, holding an EC-Council certification provides great opportunity for advancement in a US NAVY career.
The decisions of Department of the NAVY to incorporate industry recognized certifications into the Cyber IT & Cyber Security Workforce Framework ensures as our service personnel advance their careers and eventually transition to civilian life, their skills and credentials are widely recognized by the Industries they will continue to work in as Veterans.
Certifications recognized, accepted, and often funded by the US NAVY include:

Funding opportunities for career advancement are available for Active Duty NAVY personnel through the NAVY COOL program.
US NAVY approves EC-Council Certifications across 18 Occupations and over 100 Job roles
*All information represented here can be found on the NAVY COOL site. To find what EC-Council Certifications map to your eligible Job role, select “Full Credential Search” then under Credential Agency, select or search for “International Council of E-Commerce Consultants”.
To get more information or still have questions:

EC-Council Cyber Security Certifications and the US ARMY
Five EC-Council Certifications are recognized by the United States ARMY across 15 occupations. Ranging from Cyber Operations Technician to Target Digital Network Analyst. Our certifications are in use as baseline credentials across ARMY Cyber throughout intelligence as well as deployed infantry. EC-Council is proud to work with various groups in the ARMY to support the Mission of ARMY Cyber.
Certifications recognized, accepted, and often funded by the US ARMY include:

Funding opportunities for career advancement are available for Active Duty ARMY personnel through the ARMY COOL program.
US ARMY approves EC-Council Certifications across 15 Occupations
- Cryptologic Cyberspace Intelligence Collector - Analyst
- CYBER Operations Technician
- Information Protection Technician
- Military Intelligence (MI) Systems Maintainer/Integrator
- Senior Network Operations Technician
- Cryptologic Cyberspace Intelligence Collector - Analyst
- CYBER Operations Technician
- Information Protection Technician
- Military Intelligence (MI) Systems Maintainer/Integrator
- Senior Network Operations Technician
- Counterintelligence Agent
- Cyber Operations Specialist
- Infantryman
- Information Technology Specialist
- Nodal Network Systems Operator-Maintainer
To get more information or still have questions:

EC-Council Cyber Security Certifications and the Marine Corps
Five EC-Council Certifications are recognized by the United States Marine Corps in 79 Cyber Security Job roles, across 17 occupations. Ranging from Cyber Security Technician, to Signals Intelligence and Electronic Warfare Operator, to Cyber Security Chief.
Certifications recognized, accepted, and often funded by the US Marine Corps include:

Funding opportunities for career advancement are available for Active Duty MARINE CORPS personnel through the Marine COOL program.
US ARMY approves EC-Council Certifications across 15 Occupations
To get more information or still have questions:

EC-Council Cyber Security Certifications and the US Air Force
Four EC-Council Certifications are recognized by the United States Air Force in 150 Cyber Security Job roles, across 8 occupations. Occupations are recognized in fields like; Cyber Transport Systems, Intelligence, and Cyber Warfare Operations.
Certifications recognized, accepted, and often funded by the US AIR FORCE include:

Funding opportunities for career advancement are available for Active Duty AIR FORCE personnel through the AIR FORCE COOL program.
To get more information or still have questions:
Qualifying Chapter 31 (VR&E) United States Veterans may use their benefits to quickly study and attempt industry certifications and career training.
Please click the "Contact Us" button below and enter "GI Bill" in the "Your Question" box. An EC-Council representative will contact you with more information regarding how we can support you.
To get more information or still have questions:
About the Exam
Exam Name: CEH 312-50 (ECC EXAM), 312-50 (VUE)
Number of Questions: 125
Test Duration: 4 Hours
Test Format: Multiple Choice
Test Delivery: ECC EXAM, VUE
Think You're Ready?
Take the Quiz to test your readiness!
Passing Score
In order to maintain the high integrity of our certifications exams, EC-Council Exams are provided in multiple forms (I.e. different question banks). Each form is carefully analyzed through beta testing with an appropriate sample group under the purview of a committee of subject matter experts that ensure that each of our exams not only has academic rigor but also has “real world” applicability. We also have a process to determine the difficulty rating of each question. The individual rating then contributes to an overall "Cut Score" for each exam form. To ensure each form has equal assessment standards, cut scores are set on a "per exam form" basis. Depending on which exam form is challenged, cut scores can range from 60% to 85%
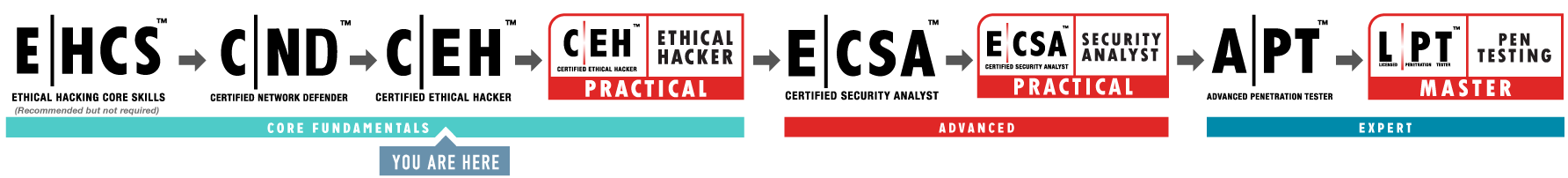
About the Certified Ethical Hacker Master
To earn the CEH Master certification, you must pass the CEH Practical exam. The CEH Practical Exam was designed to give students a chance to prove they can execute the principals taught in the CEH course. The practical exam requires you to demonstrate the application of ethical hacking techniques such as threat vector identification, network scanning, OS detection, vulnerability analysis, system hacking, and more.
The CEH Practical does not contain simulations. Rather, you will be challenging a live range which was designed to mimic a corporate network through the use of live virtual machines, networks, and applications.
Successfully navigating and completing the challenges found in the CEH (Practical) Exam is the next step after attaining the Certified Ethical Hacker (CEH) certification. Successfully passing both the CEH exam and the CEH Practical will earn you the additional certification of CEH Master.
CEH Master Credential Holders are proven to be able to:
- Demonstrate the understanding of attack vectors
- Perform network scanning to identify live and vulnerable machines in a network.
- Perform OS banner grabbing, service, and user enumeration.
- Perform system hacking, steganography, steganalysis attacks, and cover tracks.
- Identify and use viruses, computer worms, and malware to exploit systems.
- Perform packet sniffing.
- Conduct a variety of web server and web application attacks including directory traversal, parameter tampering, XSS, etc.
- Perform SQL injection attacks.
- Perform different types of cryptography attacks.
- Perform vulnerability analysis to identify security loopholes in the target organization’s network, communication infrastructure, and end systems etc.
About the Exam
- Exam Title: Certified Ethical Hacker (Practical)
- Number of Practical Challenges: 20
- Duration: 6 hours
- Availability: Aspen – iLabs
- Test Format: iLabs Cyber Range
- Passing Score: 70%
How to Prepare for CEH (Practical)
While we strongly recommend that candidates take the CEH and pass the CEH exam, there are no predefined eligibility criteria for those interested in attempting the CEH (Practical) exam.
Exam Proctoring:
We know that traveling to an exam center can be difficult for many. We are pleased to announce that you can take the CEH (Practical) exam from the comfort of your home, but you need to be prepared to be proctored by a dedicated EC-Council Proctor certification team under strict supervision.
The exam dashboard code is valid for 3 months from the date of receipt. Should you require the exam dashboard code validity to be extended, kindly contact [email protected] before the expiry date. Only valid/ active codes can be extended. The exam needs to be scheduled a min 3 days prior to the desired exam date. Exam slots are subject to availability.
Exam Validity
The trust that the industry places in our credentials is very important to us. We see it as our duty to ensure that the holders of this credential are proven hands-on, ethical hackers who are able to perform in the real world to solve real-world challenges. As such, the CEH (Master) is designed as a hands-on exam that will test the skills of the ethical hacker BEYOND just their knowledge. This exam is a proctored, practical exam that can last up to 6 hours.
We know that traveling to an exam center can be difficult for many. We are pleased to announce that you can take the CEH (Practical) exam from the comfort of your home, but you need to be prepared to be proctored by a dedicated EC-Council Proctor certification team under strict supervision.
Choose A Training Option
Add the Mobile Security Tool Kit to Your Training
For the past several years we have offered our training on a mobile device so that you can take your training with you and eliminate the need to stream the videos. This device is the next generation mobile device. This is a fully loaded pen test tool kit comes equipped with a custom Linux Hacking OS and, wait for it… we can load your course (or 2) onto the device. In the sage words of Ray Bradbury, “Something Wicked This Way Comes.”
Specs
- Broadcom BCM2837B0, Cortex-A53 (ARMv8) 64-bit SoC @ 1.4GHz Mobile System with Case
- 1GB LPDDR2 SDRAM
- 7 inch Touch Screen Display
- 2.4GHz and 5GHz IEEE 802.11.b/g/n/ac wireless LAN, Bluetooth 4.2, BLE
- Gigabit Ethernet over USB 2.0 (maximum throughput 300 Mbps)
- Extended 40-pin GPIO header
- Full-size HDMI
- 4 USB 2.0 ports
- CSI camera port for connecting a Raspberry Pi camera
- DSI display port for connecting a Raspberry Pi touchscreen display
- 4-pole stereo output and composite video port
- Micro SD port for loading your operating system and storing data, with Hacker StormOS, Raspbian-based OS included.
- 5V/2.5A DC power input
- USB 2.0 A to B Micro Power Cable. [The Storm can be powered from a 5V micro-USB source, Power Supply not included with base package.]
- Power-over-Ethernet (PoE) support (requires separate PoE HAT)
- Rollup Water Resistant Keyboard
- Field Case Organizer for all your gear