
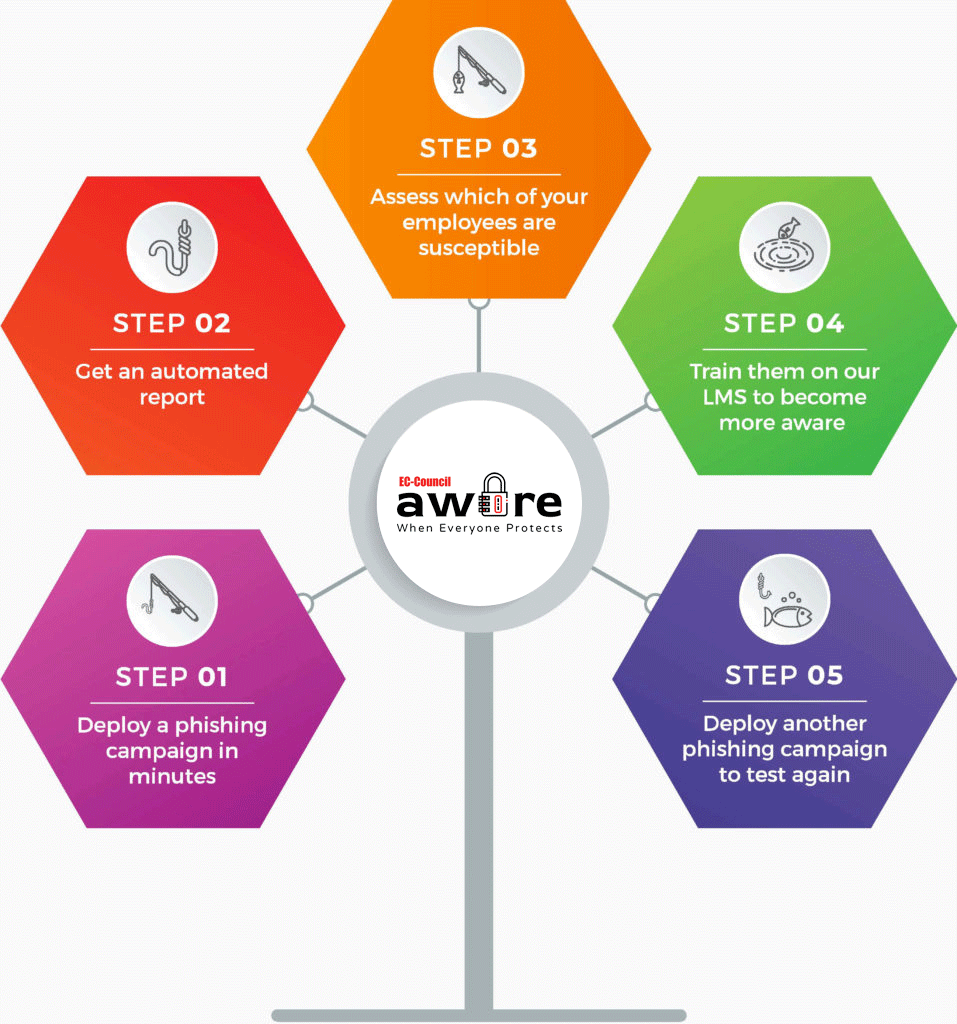
Phishing Solutions
Train Them to Think Before They Click
Research shows susceptibility to phishing emails drops almost 20% after a company runs just one failed simulation. Through accurate training, people learn, security awareness rises, and risk is mitigated with an intelligent solution like Aware.
How can Aware help?
Aware provides training to your employees, so they become better equipped to deal with any type of phishing situation. It also provides in-depth reporting so that employers can see the key areas they need to work on.
Aware Reporter
Our Aware reporting tool helps you gain visibility into your organization’s risk behavior and measure the overall risk levels across your user groups. You will also have different types of reports at your disposal, including:
- User susceptibility ratings
- Total users who have been tested
- Users who fall for the simulated attack
- Detailed campaign statistics
Learning Management System (LMS)
Education is an essential component of any security program. For a security program to be effective, it must be backed up by training to help employees make the right decisions in the face of potentially dangerous security threats.
Knowing that they have fallen for a simulated phishing attack isn’t sufficient. Employees need to understand how they were tricked in order not to make the same mistake again.
By integrating testing and security awareness trainings, Aware’s LMS can help you to manage and deliver your security awareness program.
Interactive Training Materials
Reinforcement is essential in changing behavior. Our training materials include:
- Short, engaging, on-demand videos that hold users’ attention and deliver important messages
- Games that improve engagement and increase motivation
- Fun quizzes to track user’s learning
Track Your Employees’ Security Education
Our LMS makes it easy to monitor your employees’ progress and target areas of concern. Keep track of which employees have started, completed or have not begun their assigned modules.
In doing so, you will be able to refine your organization’s awareness program, besides driving continuous improvements.
Just-In-Time Training
Users who fall for simulated attacks will be automatically directed to a landing page with an appropriate training material related to the area that needs improvement. You may also manually assign relevant trainings to specific individuals.
Import Your Own Content
Does your organization already have its own training program? No problem. You can easily import your own learning materials into our LMS.
Interactive Training Materials
Education is essential to any security program. However, we believe that for education to be effective, employees need to be able to remember and apply whatever they have learned. Our security awareness training content, which includes interactive training modules, gamification, quizzes, and videos, is designed to promote active learning and optimal retention.
Some of our standard contents includes:
- Ransomware
- Phishing
- Social Engineering
- The human factor
- Device security
- Passwords
- Cyberattacks
Aware Training Features
Interactive Quizzes
Test whether your employees understand and retain information from what they have learned.
Gamification approaches
Boost cybersecurity awareness with games to promote a fun and memorable learning experience.
Customizable Training Courses
Select and customize which courses your employees take by adding and removing topics.
Automatically Assign Courses
Test whether your employees understand and retain information from what they have learned
We are offering Aware through iClass because we believe that mitigating cybersecurity risks, especially those involving human error, often begins with changing the cybersecurity hygiene of end-users. Our solution, which combines simulated phishing attacks with set-and-go training modules, can help improve awareness, alter user behavior and reduce the risk associated with social engineering attacks.
Reduce the cyber risk to your organization with Aware.
Our phishing simulations mimic real-life attack scenarios that teach your employees to spot phishing scams and avoid the hefty cost of a data breach.
01
Cybersecurity is no longer just the responsibility of the IT department. All employees must do their part to keep the company’s data safe.
02
Employees are vulnerable to malware through their use of company email, browsing the web, social media, or other network software.
03
Employees must be able to recognize the types of attacks that may compromise the company’s network security.
04
Employees must be prepared to use best practices against data breaches and malware infiltration as part of a risk prevention program.
What is Phishing?
Phishing is a cybercrime in which unsuspecting victims are contacted by email, telephone or text message by somebody posing as a credible source to lure victims into providing sensitive information such as banking and credit card details, and passwords. Click on the topics below to read more about each.
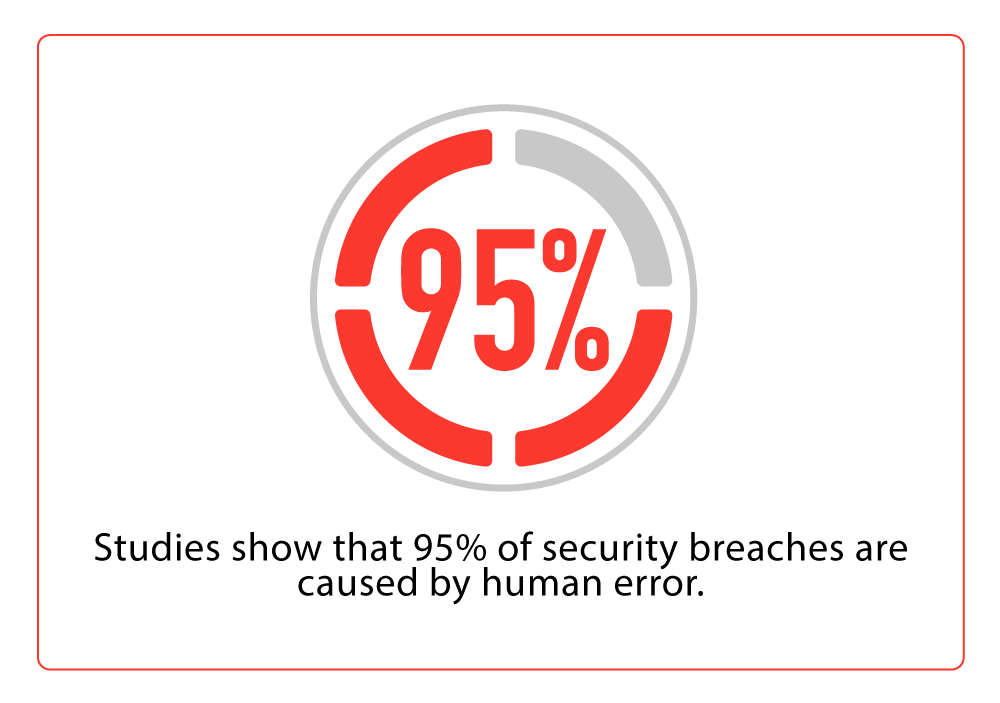
Humans are the weakest link in the information security chain, and cybercriminals know this better than anyone else.
Phishing has been going on for many years now, yet many users continue to fall prey to tactics that bait victims into revealing their personal information. There is a reason why this type of cyber threat is so prevalent and dangerous: besides being relatively inexpensive, it is also very easy to execute.
Identifying an email scam is not always a straightforward process. This is where OhPhish comes in! Our phishing simulations mimic real-life attack scenarios that teach your employees to spot phishing scams and avoid the hefty cost of a data breach.
SMiShing or SMS phishing is a variant of phishing scams. It basically uses text messages to trick users into divulging their confidential information.
As texting is one of the most common methods of communication for many users, this inevitability makes it an irresistible target for many cybercriminals. SMiShing has become one of the main tools in a scammer’s arsenal, partly because it is so easy to wield and requires little technical knowledge.
SMiShing typically follows the usual phishing route. Each text contains a link that directs the target to a website and asks them to fill in their details or prompts them to download malware onto their system. However, as opposed to a standard phishing attack, the success rates are higher with a SMiShing attack because users are not conditioned to receiving spam on their mobile phones.
Voice Phishing, commonly known as vishing, is the telephone equivalent of phishing. Like its email counterpart, vishing tricks users into revealing confidential information over the phone by posing as a trusted entity. Vishing scams can be very convincing because these callers are usually experts in their respective fields.
Vishing often begins where phishing ends. For instance, you click on a link for an advertisement that relates to your own personal interest. The link, which hides embedded malware, triggers a lock-up component that only a helpful “technical” person can help you with. So, you call the number you see and spend some money to remediate the problem. Little did you know, it was all just part of the scam, and the company that you just called was the culprit that created this problem in the first place.
Scammers often use caller ID spoofing to lend them credibility when they send out calls to potential victims. As a result, victims are compelled to pick up the call, especially if it appears to be coming from a legitimate source or from a number similar to their own. Regardless of the source, most vishing attempts would convince victims to give up confidential information. This information is then used for identity fraud or to steal money from their accounts.

